We value our customer’s security and work hard to ensure that our platform and procedures are focused on security of our clients data. A PayrollHero account contains all employee information and confidential material. For that reason, we take security, encryption, and system permissions very seriously.
We value our customer’s security and work hard to ensure that our platform and procedures are focused on security of our clients data. A PayrollHero account contains all employee information and confidential material. For that reason, we take security, encryption, and system permissions very seriously.
Below we have listed a complete guide of our security processes for your reference.
User Security
- Mutual Non-Disclosure Agreement
At the onset of our business relationship, we sign a mutual non-disclosure agreement as part of our commitment to your company confidentiality.
- Password Strength Policy
We have a Password Strength Policy which ensures that a PayrollHero user will be able to log in with high security measures.
We require all passwords to use the following:
– One lowercase letter
– One uppercase letter
– One number
– 8 characters in total for password length
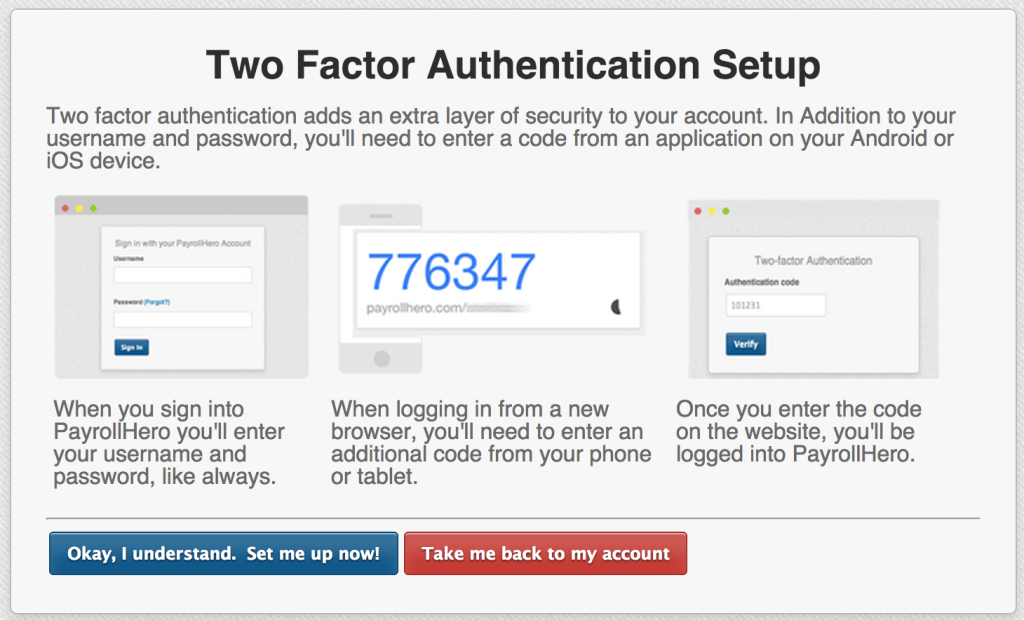
- Two Factor Authentication Log In
As an added layer of security for users, we have implemented a Two Factor Authentication (2FA) log-in, which makes logging in more safe and secure.
With 2FA, users are blocked from sharing passwords – giving the user complete ownership and responsibility for his or her personal account.
Every time a user logs in, they get a time-based, one-time password to authenticate the log in process. This password changes every time you log in, and only you, the user, will be able to know this generated password.
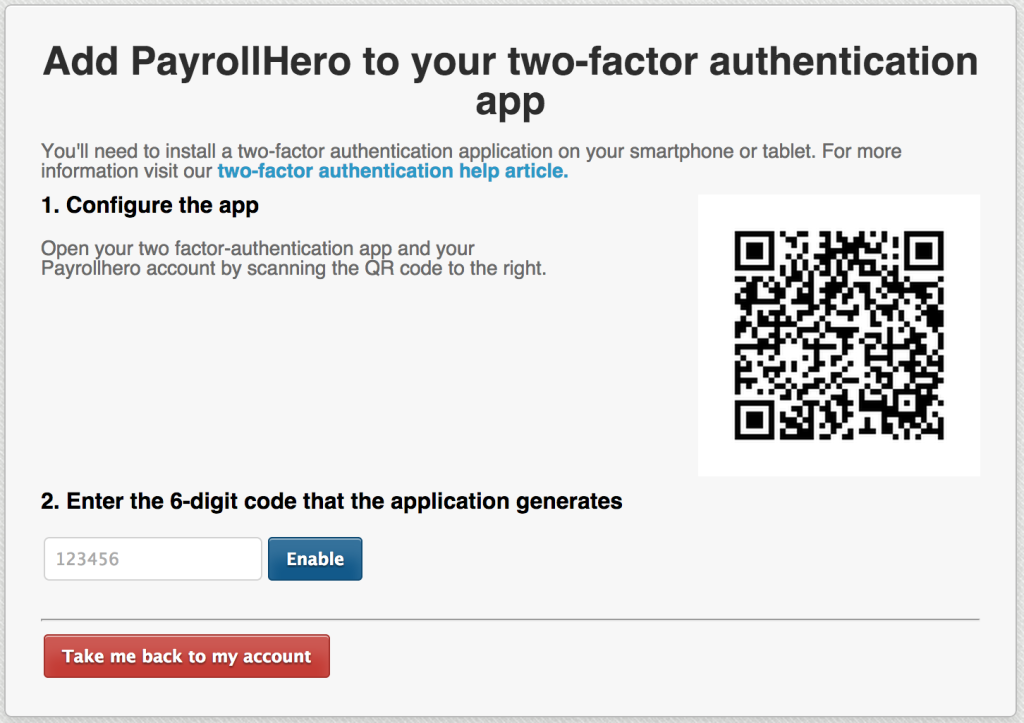
To enable 2FA, you would need a device, usually a smartphone, and an app to generate these one-time use passwords. Here are some of our recommended apps:
- Google Authenticator
- Authy (recommended if you want to use multiple devices e.g iPad, desktop)
Click here for a complete guide on how to set up Two Factor Authentication for your PayrollHero account.
Platform Security
- Encryption at Rest
All data within PayrollHero is encrypted in transit and at rest, meaning that it is not only encrypted when moving from application to application but it is also encrypted when idle.
- HTTPS
All communication in and out of the PayrollHero platform is done through HTTPS. “Hypertext Transfer Protocol Secure (HTTPS) is a communications protocol for secure communication over a computer network, with especially wide deployment on the Internet”.
** For both security and non-security incidents, we have employ an urgent and critical process that brings a certain priority level to the team. There is an incident commander appointed during any of these incidents and is responsible for involving the necessary resources.
Architecture
The PayrollHero System is designed to only expose access to customer facing services. All other access requires an encrypted administrator connection.
- Only vetted senior staff members have access to production data.
- All access requires encrypted access to the system.
- All access to the system requires either an encrypted VPN connection or two factor authentication to access anything.
- All access to production data is logged.
- All systems are isolated from each other, regularly replaced, and security patches are applied as soon as they are available.
Customer data is stored on a multi-tenant environment, as such it does exist within the same databases. Extreme care is taken to never allow customer data to get mixed up.
The PayrollHero system is designed to deal with server failures. We perform offsite backups, and frequent onsite backups. We also have an offline mode for the clock in/out feature.
If you want to learn how to use TeamClock while offline, click here for a quick tutorial.
Servers
In an effort to ensure that all your data is kept secure, we only use one of the best names in server and cloud computing – Amazon.
Technically speaking, we secure our data with the following services.
PayrollHero utilizes AWS Services that are ISO 27001 and PCI DSS L1 Certified:
- Amazon Web Services Elastic Compute Cloud (EC2)
- Amazon Web Services Simple Storage Service (S3)
- Amazon Web Services Relational Database Service (RDS)
- Amazon Web Services Elastic Load Balancing (ELB)
- Amazon Web Services Identity and Access Management (IAM)
- Amazon Web Services Elastic Block Storage (EBS)
PayrollHero will use commercially reasonable efforts to make the PayrollHero platform available with a monthly uptime percentage of at least 99%, in each case during any monthly billing cycle (the “Service Commitment”). In the event PayrollHero does not meet the Service Commitment, You will be eligible to receive a Service Credit as described below.
Service Level Agreement
Service Credits are calculated as a percentage of the total charges paid by you (excluding one-time payments such as upfront payments) for the monthly billing cycle in which the platform was unavailable.
- If the monthly uptime percentage drops below: 99%
- Service Credit Percentage: 20%
- Service Credits are applied to Your next months invoice.
- To receive a Service Credit, You must submit a claim by opening a support case (support@payrollhero.com).
To be eligible, the credit request must be received by us by the end of the second billing cycle after which the incident occurred and must include:
- the words “SLA Credit Request” in the subject line;
- the dates and times of each unavailability incident in respect of which You are claiming;
- the affected PayrollHero account;
- and your request logs that document the errors and corroborate Your claimed outage (any confidential or sensitive information in these logs should be removed or replaced with asterisks).
Our most up to date Terms of Service.
If you have any other questions about our confidentiality, data security, or encryption, please feel free to contact us at support@payrollhero.com.